LinkedIn has a fake profile problem, with fake profiles being set up on an industrial scale. It is now the number one source hackers use to research potential victims. Here’s how to spot fake profiles and how to protect yourself and your business.
We all get them. Those connection requests from LinkedIn (especially after you have polished your LinkedIn profile). But what do you do with the requests? Should you automatically connect?
Hold your horses! We need to have a chat about stranger danger.
You know those lectures you give your kids about chatting to strangers on the net? You need to sit yourself down and have a serious talk with yourself about chatting to strangers.
Now, this may surprise you, but not everything and everyone you see on the internet is true.
LinkedIn has an increasing problem with fake profiles created by hackers, spammers, spies and trolls, and unfortunately, most small business owners are too trusting when it comes to LinkedIn.
The head of MI5 in the UK, Ken McCallum, said that malicious profiles linked to hostile states are being created on “an industrial scale.”
People can easily set up a fake profile with just a few clicks – and the good-looking twenty-something female web designer you thought you were connecting with in the UK suddenly turns out to be a middle-aged hacker in India.
While LinkedIn is active in removing fake accounts, when there are 645 million members, all governed by a pinkie promise system to tell the truth, abuses will happen.
There are no checks and balances. LinkedIn works on an honour system so people can make up any details they like (including companies they have worked with), and there are no notifications or checks done as to whether the information is true or false.
Why Hackers Want to Connect
Before we explore how to spot the baddies, let’s start with why they do it in the first place.
LinkedIn is a treasure trove of personal information, including your email addresses and phone numbers.
The most common reason hackers/spammers want to connect is so they can harvest your personal details by simply going to your profile and copying and pasting the information you generously make available to your connections.
At the most superficial level, these details can be sold to spammers to bombard you with ads for the latest male enhancement pill or potion.
Spear Phishing
However, in recent years, spammers and hackers have turned to LinkedIn as their number one research source to gather information about organisations to create targeted spear-phishing attacks,
Spear phishing is where a highly targeted and customised email or other forms of electronic communication is sent to a specific individual.
This communication often uses information gathered by the hacker in a way that builds trust and lulls the person to feel that the communication is genuine.
For example, they may reference a conference or event you recently attended or mention a close friend or contact in another work team. They make you believe that the email comes from a credible source to get you to click on a link (that leads to a malware or virus-infected site) or to part with sensitive information.
Whaling
If you are in a particularly sensitive role, this form of spear phishing is known as whaling. Whaling specifically targets high-level executives, people with access to payroll or financial systems, cybersecurity people, politicians, celebrities or people with high-level security clearances.
Hackers connect with you on LinkedIn using fake profiles and then work their way through your profile to find information to use in spear-phishing attacks for you.
If you are not the end target, some of your connections may be. Hackers browse through your connection list (if you don’t have it locked down) to explore all your connection’s profiles and their contact information. They then use that information to spear-phish your connections.
They use information such as titles, reporting structures and emails to help impersonate senior management in spear-phishing campaigns to get someone to click a malware-laden link or get an employee to take action such as transfer funds or pay a fake invoice that goes to the hacker.
If that isn’t enough, they can contact your connections directly and send LinkedIn mail to them, suggesting that they had been chatting with you and that you thought a particular link (leading to a malware-infested site) or document (filled with ransomware) would be of interest to them.
Spies connect with potential targets, often posing as a recruiter or event organiser.
They are often highly flattering in their praise of the person and promise highly lucrative job or speaking opportunities. They quickly move the discussion to non-traceable communication channels and then go through the process of gradually moving the person to share confidential or classified information.
In effect – spies use LinkedIn to recruit sources, other spies or double agents.
This rarely works out well. In the US, a former CIA officer was sentenced to 20 years in prison after being convicted of giving secrets to China following an approach via LinkedIn.
How to Spot Fake LinkedIn Profiles
Some fake profiles can be easily identified with a little bit of digging. If any connection requests match these warning signs, they should get the automatic bin and block treatment.
Pictures Check
Fake profile pictures come in three kinds:
Photos of famous and semi-famous people: Unfortunately, George Clooney will never be sending you a LinkedIn request.
Stock photos: If the person has super white teeth and is carrying a piece of technology or is wearing a headset, they are probably a stock photo and not an actual breathing human being.
Photos of realistic-looking people: In this example, the hackers used the photo of a real person in a fake profile (we blurred her face because it was a fake profile using the photo of a real person).
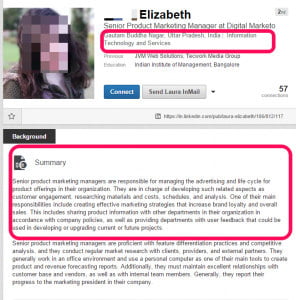
Before you accept any request, right-click the photo and click “Search Google for this image” (if you are using Chrome).
If you are using other browsers, then follow the instructions from Google https://support.google.com/websearch/answer/1325808?hl=en
You should then be able to see where else the image can be found around the net. Often you will find the photo appears in hundreds of stock libraries or newspapers or across many websites as representing their call centre operator. You can safely assume these are not real connections.
But what if the photo is of a real person? This is where you do a bit more digging. Scammers rarely set up the same profile on multiple accounts so check out the person’s photos on Twitter or Facebook. If anything looks suss then reject the request.
Unfortunately, Artificial Generators are available on the net that gets around any photo research you may do.
This Person Does Not Exist is a site where every time the page is refreshed, an algorithm known as a generative adversarial network creates hyper-realistic portraits of false people who do not (and never have) existed. This means you will not find any matches of that person’s photo around the net, which can lull you into a false sense of security.
Here’s one I prepared earlier. Looks real doesn’t he? Nope! He is a fake.

Connection Check
If the person only has a small handful of connections – then keep digging. They may be legitimate but be cautious.
If they have 500+ connections, then they MAY be legitimate.
If enabled, then check out their shared connections. If the only connections in common are from friends that you know say yes to everyone, you may want to keep digging.
Unfortunately, hackers are also onto this check and now buy connections to hit the magic 500+ number.
How to Geek did an interesting expose on how easy it was to set up a fake LinkedIn profile and buy connections. Salutary reading!
Background & Job History Check
Most LinkedIn profiles will not win Pulitzer prizes with their writing, but zero details are a red flag. Just say no!
If you want to improve your own LinkedIn profile – this may help: https://www.heartcomms.com.au/linkedin-profile-tips/
The other red flag is where they have copied and pasted generic typical role descriptions for the role they are impersonating. The spammers are doing this to get through any automated scanning software. Often they copy the text into multiple sections. Continue just to say no!

An easy check is to see if the company exists. Many fake accounts include fake companies that do not exist.
However, remember there is no alert to companies to let them know when someone claims to have worked with them. Spammers and hackers may also claim to work at legitimate companies related to yours to build trust.
Education Check
Check if the qualifications look legitimate.
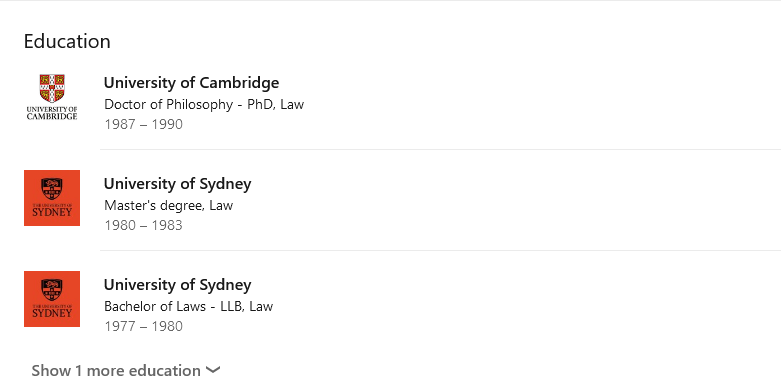
Copying and pasting information from a prospectus is a danger sign. It shows they know how to cut and paste – but probably does not show that they actually did that course at Uni (particularly as in this case they copied a graduate program and the profile had no undergraduate qualifications).

There are also no notifications to educational institutions of claimed degrees. Here is an example from a fake account where the person has claimed an impressive series of qualifications.
Skills & Endorsements Check
Love them or loathe them, endorsements for skills do give clues about a person. If someone has 100+ connections and only three endorsements, you can bet your house that the endorsements came from other scam profiles.
However, people can buy endorsements when they buy connections, so even skills and endorsements are not a valid measure.
Location Check
If you are a local business with a local presence, then it is unlikely that someone from Pakistan or Estonia will want to connect with you on LinkedIn. Check to see where the person is claiming they are from.
Can You Spot a Faked Profile?
While these checks will help you weed out the obviously fake profiles, high-level fakes are almost impossible to identify.
Security In Depth, a cybersecurity company, has created a fake Managing Partner profile for a law firm (I won’t share the exact details of the profile) that they use in their education and training campaigns.
They did not buy followers or endorsements for the profile, but at last look, over 500 legitimate CEOs and legal people had connected to the profile.
I shared that profile with legal colleagues of mine to see if they would have connected with the fake profile and had a 100% resounding “Yes.” (Followed by embarrassed comments about how my colleagues need to undertake LinkedIn training to spot fakes).
What Do You Do When You Spot A Fake LinkedIn Profile?
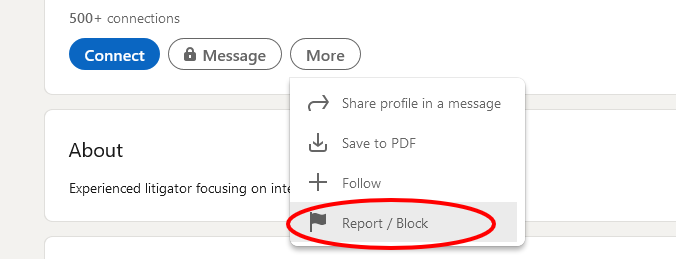
If you spot a fake profile, click the more button and then click “Block or Report.” Do everyone a favour and help weed out the scammers.
LinkedIn Tips To Increase Security
* Never accept LinkedIn invitations from people you don’t know without doing due diligence first. Always be sceptical of why someone wants to connect with you. Do they genuinely want to connect, or do they just want to flog something to you (marine collagen lady I AM looking at you) or scam you?
* Never click on any links in LinkedIn messages to things like Google or Dropbox documents, or open any attached Word or PDF documents.
* Enable Dual Factor Authentication on your LinkedIn account. I use and recommend Authy as a robust and easy to use Authenticator App.
* Change your login password every six months.
* Never share personal or confidential information via InMail.
* Edit your contact information and remove your phone number from your contact card. (Click on your profile and the Contact Info link. Then click the pencil icon and delete the phone number and click save).
* Work your way through the Settings and Privacy Tab – especially all the Visibility Tabs. Be aware that the settings vary depending if you are on the app or on desktop. Use the desktop version as you have more options than on the app.
I have my visibility options set to:
- Profile Viewing Options – Anonymous LinkedIn Member
- Story Viewing Options – Anonymous LinkedIn Member
- Edit Public Profile – I edited my public visibility to basic and adjusted the toggles for things shown to non-LinkedIn members.
- Who can see or download your email address? I have it set to visible to me and toggle who can download my email address to their data export to no.
- Connections – Allow your connections to see your connection list set to no. (Regardless of what you choose here, your first-degree connections will always be able to see mutual connections.)
- Last name – I show it, but you can change to first name and initial if you are very security conscious.
- Representing your organisation and interests – Set to No.
- Profile visibility off LinkedIn – Set to No.
- Profile discovery using email address – Set to Nobody.
- Profile discovery using phone number – Set to Nobody.
- Manage Active Status – Set to no one.
- Share profile updates with your network – Set this to no (more so you don’t annoy people when you fix a typo in a profile and LinkedIn announces it to the world).
A few more tweaks:
- Communications – Messaging Experience – Allow Linked In partners to show you sponsored messages -Set to no.
- Research Invites – Set to no.
- Read receipts and typing indicators. Personal choice, but I set it to no.
- Advertising data – I turned off everything here. There are over a dozen ways they gather your data to market, so feel free to say no to everything.
* Do NOT under any circumstances click on any links in a suspect LinkedIn bio, especially if the links are shortened, and you can’t see where they are going. Scammers often cloak their links and take you through fields of malware-infested sites.
* Ignore all emails allegedly from LinkedIn (the organisation) that land in your inbox as spammers and hackers often try to impersonate LinkedIn. Any legitimate LinkedIn email will have a copy saved in the notifications section of your account. Read your LinkedIn notifications via your account (but don’t click the link in the email to get there. Type in LinkedIn in your browser).
* Periodically search your company name on LinkedIn and review the profiles of people who claim to have worked with you. If you spot any fakes, report them to LinkedIn.
What If You Find Yourself on Linked In?
One of the most surreal experiences you can have is discovering that someone is impersonating you on LinkedIn with your photo, name, or details.
These need more direct action. Report the impersonation, and DON’T click on any links in their/your bio in a mad panic to find out who they really are!
Last Thoughts
Many people love LinkedIn as a way to connect with other business owners. Unfortunately, it has significant cybersecurity problems right now. All people who use LinkedIn need to be aware of the problems and reduce their risk when using the platform.





